- The scope of the ‘siegeware’ threat
- Creating powerful malware isn’t as expensive as it may seem
- A hacker hijacked Nest devices in a family home
- Exfiltrating data through a fish tank and modem routers
- Google hacked by its own employee
- Hospital data breach left 1.5 million patients exposed
- How to outsmart hackers and protect the system
- Every connected device is a potential threat
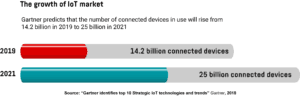
Most people wouldn’t consider their heating, ventilation, and air conditioning (HVAC) system as a prized target for cyber criminals. After all, a successful hacking attempt could go as far as making us uncomfortable for a few minutes until we fix the problem. This wishful thinking, however, is what hackers are counting on. As we deploy a growing number of connected devices such as smart HVACs, intelligent cameras, and smart doorbells in our homes and offices, the complexity of the Internet of Things (IoT) ecosystem increases. Gartner, a research and advisory company, predicts that 25 billion connected devices will be in use by 2021. And many of these IoT devices will interact with each other through house automation servers like FHEM (Freundliche Hausautomatisierung und Energie-Messung) and Home Assistant, making our lives more comfortable, but less secure.
Sure, having tech that automatically turns on the air conditioner and lights as people enter the room is convenient, but building automation systems (BAS) that integrate connected ‘things’ are often inadequately secured and configured. Hackers easily breach them by, for instance, finding a weak spot in an unprotected web login page of a fire detection system. Once inside, hackers move to take over other parts of the BAS as well and can shut down the alarm or heating systems and demand ransom payment. This threat, also known as ‘siegeware’, is growing in severity, and many companies and individuals have already fallen victim to these attacks.
The scope of the ‘siegeware’ threat
According to ForeScout, a cybersecurity firm, the number of vulnerabilities in automation systems is constantly increasing. Hospitals and schools are particularly unprotected from cyber-attacks, and they operate as much as 8,000 highly vulnerable devices. And taking full control of these devices can have major consequences.
ForeScout explains that control over smart devices can eventually provide hackers with access to private financial files and information stored in data centres. Also, they can listen to conversations, review camera streams, delete files, reprogram automation rules, distribute malware, and provide unauthorised individuals with physical access to the building. And although many of the vulnerabilities that hackers exploit are well known, only about half of them in industrial and IoT systems have been patched. What’s worse, even hackers with limited resources can develop effective malware and hack smart buildings.
Creating powerful malware isn’t as expensive as it may seem
For instance, it took ForeScout only $12,000 to develop proof-of-concept malware to show how easy it is to hack a smart building. In that process, the security experts first spent some time analysing various automation systems and looking for weak spots. They initially found eight vulnerabilities and opted to exploit two, both of which were already known to the vendor. In the next stage, they wrote the code in the Golang programming language “with the final payload developed in Java”. The file size was only two megabytes and could easily run on devices with limited capacity.

They then deployed the malware to exploit vulnerabilities in IP cameras and gain a foothold in the network. After that, the malicious code moved through various parts of the system, allowing the attacker to infiltrate the central database, add new users, and grant them the privilege of physical access to the building. ForeScout researchers were also able to delete files and disrupt BAS operations, while the malware could survive a reboot of the system and remove traces of infiltration by editing log files. Once the test was completed, the company noted that “we are confident that this is well within the reach of many groups of actors with less positive intentions than ours.”
A hacker hijacked Nest devices in a family home
Arjun and Jessica Sud from Lake Barrington, a village in the US state of Illinois, certainly agree with ForeScout, as they were victims of a malicious cyber criminal. He hacked their Nest cameras, speakers, and thermostat, and, at first, talked to their 7-month-old baby. As Arjun grabbed the kid and went downstairs, he noted that the temperature, which was usually set to around 22°C, was turned up to 32°C. A deep male voice then yelled at him through the speaker in a security camera, using racial insults and cursing. And as soon as the voice stopped screaming, Arjun and Jessica unplugged 17 Nest devices worth $4,000 and returned them to Google’s company.
Nest says that situations like this happen because of reused passwords. It suggests everyone to make use of a two-factor verification system and regularly update the software. Christian Vezina, the chief information security officer at the mobile security company OneSpan, points out that smart home devices “are being manufactured at a crazy rate, yet they’re not being secured”. And the ramifications can be catastrophic, as hackers could learn people’s most intimate secrets and use them for blackmailing and other nefarious goals. The same danger is lurking in corporate offices equipped with connected devices, making it urgent to implement strict security protocols.
Exfiltrating data through a fish tank and modem routers
But despite all the security measures in place, creative hackers are sometimes able to overcome any obstacle. In Las Vegas, for instance, they hacked a casino through a high-tech fish tank that was connected to the internet. The malware extracted ten gigabytes of data and transferred it to a remote server in Finland. The full scope of the breach was spotted only after the staff called in experts from Darktrace, a cyber-defence company, to analyse suspicious activity. Darktrace says that “this was a clear case of data exfiltration but far more subtle than typical attempts at data theft.” This, however, isn’t the only way hackers exploit the vulnerabilities of connected ecosystems.
For instance, hackers in Brazil tried to steal people’s bank credentials by exploiting IoT devices. In one such example, cyber criminals hijacked DLink DSL modem routers and redirected all users that wanted to visit the website of Banco de Brasil to a fake website. The attack was highly sophisticated in the sense that the hijacking succeeded without editing URLs in the victim’s browser. Also, the malicious code works on both Apple and Android phones and tablets. The victims then enter their username and password, believing they’re accessing online banking accounts, while in reality, they’re delivering sensitive data to hackers.
Google hacked by its own employee
Even big tech companies aren’t immune to security flaws in IoT devices. Google’s engineer David Tomaschik, for example, found a way to control smart locks used in the company’s Sunnyvale offices by replicating the encryption key and forging commands in the office controller software made by the tech firm Software House. Even without the required RFID keycard, Tomaschik managed to open or lock the door and prevent people from entering the facility. And he could do all of this without leaving any digital traces behind.

Google moved swiftly to segment its network and shield the vulnerable code from possible outside interference. As for Software House, the company claims it’s now using a more sophisticated form of encryption known as TLS. But the existing hardware and smart lock systems at customer sites aren’t powerful enough to run the new software, which means that multiple companies throughout the world are vulnerable to cyber-attacks. Hackers can enable people to enter the premises of these companies, and, for instance, steal information or plant malware using infected USBs.
Hospital data breach left 1.5 million patients exposed
Meanwhile, cyber criminals stole the personal data of 1.5 million patients in Singapore, including their names, gender, identity card numbers, and addresses. They stole even the prescription data of Prime Minister Lee Hsien Loong. The attack took place between 27 June and 4 July 2018, as the hackers breached the network of SingHealth, Singapore’s largest group of healthcare institutions. Luckily, records such as diagnoses or test results weren’t tampered with, but the authorities paused many of the country’s Smart Nation initiatives because of the attack.
And many people fear that hackers could misuse their identities, as ID numbers are crucial for accessing various government services in Singapore. Leonard Kleinman, the senior director of IT Security for the Australian Tax Office and cybersecurity advisor to the security company RSA, says that “such data can fetch a high price”. In 2017, a stolen or lost healthcare record was worth as much as $408 on the Dark Web.
How to outsmart hackers and protect the system
As a growing number of cyber-attacks target IoT devices and automation platforms, companies and individual users should do their utmost to deny hackers a chance to inflict damage. Executing some basic security measures can yield great results. For instance, replacing default passwords with strong and unique credentials is critical, and so is regularly updating device software. And when buying new devices, it’s important to check their security features to ensure that you can easily maintain them.
Ian Heritage, an engineer at the cybersecurity firm Trend Micro, suggests that smart home and corporate buildings could benefit by “enabling encryption for storage and communications, WPA2 for Wi-Fi routers, disabling UPnP and allowing only a hardcoded list of device MAC addresses to access the network.” Furthermore, users should back up automation server configuration and prevent installations of suspicious applications. And by introducing multi-factor authentication and lockout on failed password attempts, BAS will enjoy significant protection and will be hard to breach even for a determined hacker. Most importantly, these measures will ensure that businesses know their IoT devices actually suffered a breach, as only 48 per cent of companies can spot such events.
Every connected device is a potential threat
As billions of IoT devices and sensors connect through automation platforms, they will create networks that are difficult to protect and are susceptible to software errors. Hackers will find it easier to infiltrate the system and steal sensitive data. Tackling siegeware is a priority, but success in that endeavour is far from guaranteed. There are multiple factors to consider. For instance, are law enforcement agencies ready to aggressively pursue these cases? Will victims pay the ransom? And just how many victims are hackers able to find?
There are no definite answers to these questions, but perhaps the first and most important step is ensuring that people are aware of this threat. Hackers are unscrupulous and will go as far as to hack hospitals and risk the lives of patients. They’re willing to steal personal information and use it to harm companies. With this in mind, people should improve their cyber protection and realise that any device that connects to the internet, whether a smart fridge or a smart doorbell, is a threat as much as it is a convenience. A new mindset might be the key to dealing with cyber criminals more effectively.
Share via: