Connectedness is the future – our homes, organisations, and even entire cities have undergone an extreme smart tech transformation in recent years. Intelligent infrastructure facilitates increasing digitalisation, and we’re swiftly abandoning outdated practices, replacing them with ever more efficient ones. Paperwork is increasingly replaced with digital files and the gathered data is stored on various cloud storage systems. Moving highly valuable and confidential data to virtual storage, however, isn’t without risk.

We do have strong passwords, firewalls, and software that enables smart homes and internet security and guards data from malicious attacks. But cybercrime keeps rising, causing immense damage that’s expected to reach $6 trillion annually by 2021. Unfortunately, the list of companies that experienced some type of cyber-attack is growing, and investing in cybersecurity is definitely the way to go. According to International Data Corporation projections, organisations “are expected to spend $101.6 billion on cyber security software, services, and hardware to combat these potential threats” by 2020, Forbes reports.
As new tech and new protection systems emerge, cyber criminals keep figuring out novel ways to outsmart them. However, there are ways in which we can protect ourselves. For instance, detecting vulnerabilities and implementing cyber protection on time can help both individuals and organisations to live and conduct business in safer and more secure digital ecosystems. That’s why we’ve gathered and analysed the potential cyber-threats lurking behind exciting technologies that, in most cases, aren’t immune to malware.
1. 5G technology brings cybersecurity threats
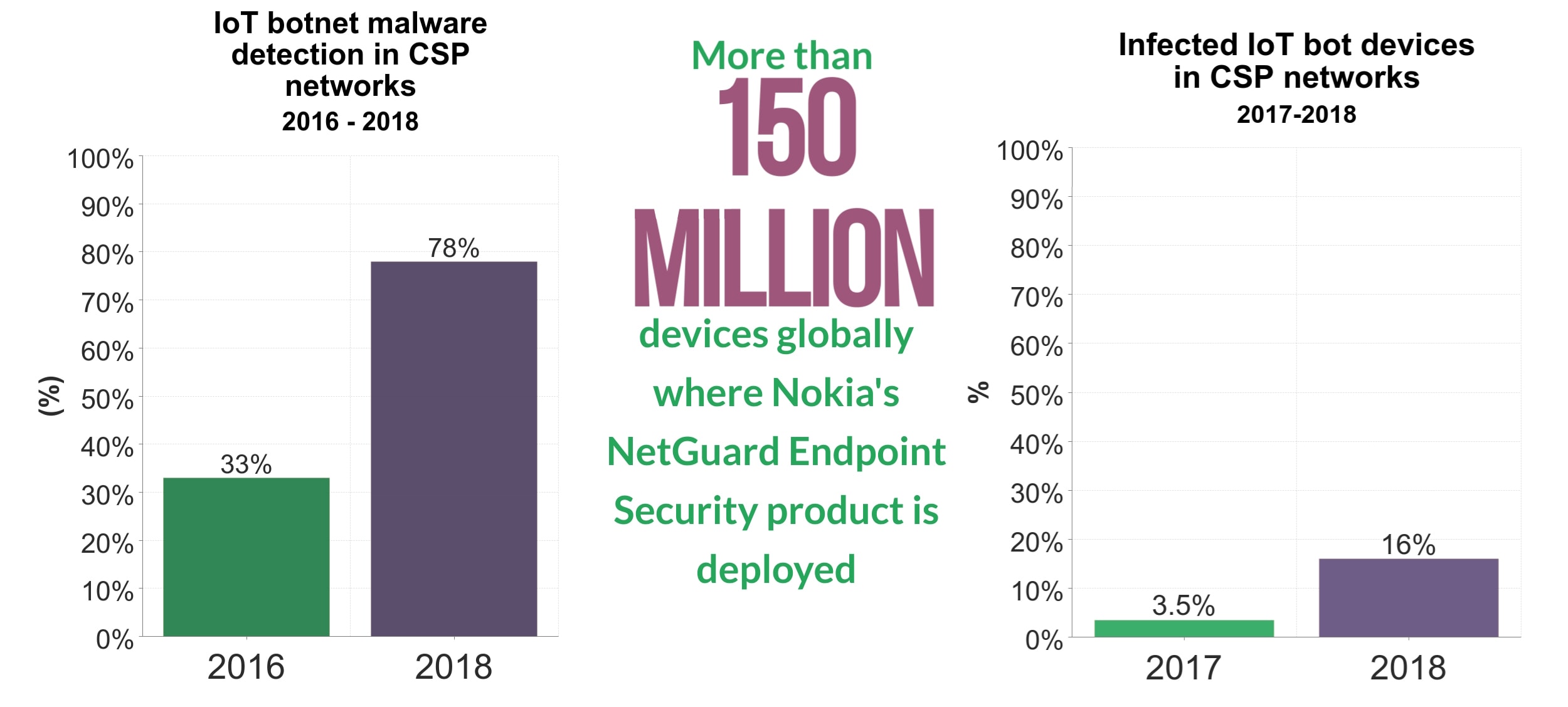
The fifth generation of wireless systems and networks, also referred to as 5G, is exciting technology. Its super-fast internet connectivity will certainly make our lives easier, and people worldwide simply can’t wait to embrace it. As Ericsson predicts, 40 per cent of the global population will be using 5G by 2024. For all the hype and excitement around this tech, however, there’s an equal number of concerns. As advances in 5G technology speed up the rate of IoT deployment, and as the IoT grows and more devices get connected to the internet, we’re under greater risk of cyber-threats. The reason for this is simple. While IoT tech manufactures are mostly focused on launching new products quickly, they often don’t pay enough attention to cybersecurity. And poor security is what makes IoT devices the perfect target for cyber-criminals. In fact, in 2018, 78 per cent of malware incidents were related to communication networks that involve IoT technology.
2. Social media is becoming a political instrument
Social media platforms have become part of our daily routine. For most people, checking Instagram or Facebook first thing in the morning has become the norm. And the popularity of social media is showing no signs of abating. Forbes reports that Facebook, the largest social media platform in the world, has two billion users. In fact, every second, five new Facebook accounts are created. But what started as a harmless technology is now increasingly regarded as more dangerous than initially thought. According to the cybersecurity company FireEye, social media can also be used to promote potentially dangerous political interests. For instance, it discovered several social media accounts that have been promoting Iranian political interests among audiences in the US, the UK, Latin America, and the Middle East. The content was mostly dealing with anti-Saudi and anti-Israel topics and was supporting the US-Iran nuclear deal. FireEye believes that social media will continue to be used as a tool to promote the political interests of foreign countries. And it’s not hard to understand how this development can potentially lead to serious conflicts.

3. Taking down the internet
The majority of internet services we use on a daily basis are vulnerable to attacks, enabling cybercriminals to hack into systems and even take down the internet. This will continue to be an issue in the future as well. As Norton predicts, 33 billion personal records will be affected by cyber-attacks in 2023, compared to 12 billion in 2018. Moreover, Cybint Solutions reveals that every year, one in three Americans are affected by a cyber incident. Clearly, cyber-attacks are becoming all too common. In fact, it’s been reported there’s a cyber-attack every 39 seconds. Since they’re becoming more sophisticated, they pose a significant threat to our society, and no one is safe. One terrifying example is the distributed denial-of-service (DDoS) attack in 2016 that took down many major websites such as Amazon, Twitter, and even CNN.
More serious DDoS attacks could cause even greater devastation. Just imagine not being able to access any website on the internet. The reason why most existing websites are vulnerable is because the Border Gateway Protocol (BGP), which drives the internet and transfers routing data between different networks, was never really designed with security in mind. BGP allows networks and autonomous systems to communicate with each other. To make this process highly secure, network operators use Route Origin Validation – cryptographically coded route data deployed to protect autonomous systems and networks from route hijacking. However, only 0.1 per cent of existing autonomous systems have deployed Route Origin Validation, while the other 99.9 per cent are at great risk of being hacked.
4. Phishing attacks are gaining traction
Online shopping brings us convenience, but it also creates opportunities for scammers. Phishing scams, for instance, targeted at capturing sensitive information like credit card numbers and passwords, are becoming a major threat. This is particularly evident in the retail world. It’s estimated that from 2017 to 2018, the number of retail phishing websites grew by 297 per cent. Phishing scams don’t involve much effort to lure the target, because scammers mostly use emails as bait. Once victims receive an email featuring a link to a website that imitates a real company, they’re already one step closer to being scammed. After they reveal their credit card information or social security number, the consequences can be devastating. The best way to protect yourself is quite simple: don’t click on every link that’s been sent to you, or at least think before you click.
5. Spear phishing is an even more sophisticated hacking technique
As phishing attacks become more sophisticated, it’s easy to become a victim of these scams. To make their scams more believable, criminals no longer rely only on sending spam emails to a wide range of users, hoping to attract someone’s interest and capture valuable information. Today’s scammers are a lot smarter, and their more advanced techniques consists of finding information about potential targets through companies’ official websites and social media platforms. Also known as spear phishing, this method allows criminals to create more convincing emails. For example, an attacker could send an email to a specific company informing it about an urgent issue. In the email, the attacker would suggest that the company checks the issue on its private network, which is basically a malicious link designed to capture the company’s private information. And it’s easy to fall for this. In fact, 91 per cent of targets get scammed via personalised emails.
6. Supply chain attacks are close to becoming our biggest cyber-threat
Both small- and large-scale business organisations are facing serious cybersecurity challenges, and supply chain attacks are one of the key threats. Almost every company today relies on third-party suppliers, and hackers are able to access companies’ systems using those suppliers. For instance, in 2013, data from 110 million Target customers was stolen in a supply chain hack. With a phishing email sent to an employee working for Target’s vendor, hackers were able to gain access to customers’ credit card information. In this case, the human factor turned out to be the biggest vulnerability. But hackers are getting smarter, and their techniques have become more advanced. Since companies heavily rely on third-party software, criminals are turning this to their advantage. They can, for instance, replace a software update with a malicious one. Without even detecting the malware, the vendor will send the update to targets and automatically infect their computer systems. Such attacks can cause huge financial losses. It’s estimated that an average software supply chain attack costs around $1.1 million. So, it’s no wonder that software supply chain attacks are expected to become a major cyber-threat in the next two years.

7. Cyber-criminals are stepping up their game with botnets
To gain more control over our computer systems, hackers are turning to botnets. Botnets are developed to infect not just one device, but millions of them. After a computer gets infected with a virus, either sent through email or shared as a pop-up ad, it allows the hacker to remotely control the computer and attack other systems as well. Such incidents are becoming increasingly common around the world. In the second quarter of 2018, botnet attacks occurred in 74 countries. As Channel Partners reveals, China, Hong Kong, and the US experienced most ot these attacks. The reason why botnets cause so much headache to cybersecurity specialists is because they’ve advanced so much over time, so it’s not easy to detect whether your computer system has been infected with such a virus. And as this tech continues to develop, it will become even harder to identify.
8. Malicious bots are impacting the global economy
The number of mobile tech users is growing at a steady pace. And just like any other technology today, mobile tech isn’t immune to cyber-threats, either. What seems to be the biggest cyber risk for mobile devices nowadays are mobile bots, malicious programs that allow hackers to go about their criminal ways – like taking over your account or stealing your identity. According to a study released by the San Francisco-based firm Distil Networks, 5.8 per cent of mobile devices used worldwide are infected with these programs. The same study reveals that at least 15 million devices in the US are infected with mobile bots. The biggest problem is that these bad bots are designed to operate in secrecy, so users often don’t even realise their device is being used for malicious activities. Another potential use for mobile bots is price scraping, through which hackers can acquire pricing data from e-commerce websites. All this has a measurable effect on the world economy.
9. IoT botnets could lead to power grid failures
IoT innovations give us greater control over our homes and cities, but as we enjoy ever greater convenience, the risks of cybersecurity issues also increase. Recently, a group of researchers from Princeton University revealed that hackers could use electricity-consuming devices connected to the internet to attack the power grid and cause blackouts. Referred to as “manipulation of demand via IoT” (MadIoT), such an attack targets the power demand side rather than the supply side. The researchers claim that hackers could create an imbalance between demand and supply by turning a lot of IoT devices on or off at the same time. This can disrupt the performance of generators at power plants and eventually lead to blackouts. A simulation model shows that a 30 per cent increase in power demand can lead to generator failure. MadIoT attacks use botnets to take control of high-wattage IoT devices like heaters or air conditioners. Botnets can easily be replicated and are hard to detect, which makes MadIoT attacks even more appealing to hackers.
10. Torii, the most sophisticated botnet ever created
As botnet tech keeps advancing, it’s easy to understand why botnets are seen as one of the biggest cyber-threats to our society. At the end of 2017, researchers from Avast witnessed the activation of a new and highly sophisticated IoT botnet called Torii. This malware strain operates on a wide range of devices and digital architectures. Once a computer, smartphone, or tablet gets infected with Torii, the hacker is able to steal sensitive data from the device, execute codes, and deliver commands to the device through encryption. Unlike other botnets, Torii uses more sophisticated techniques to take over the compromised device. Torii can’t be easily detected, and to maintain its presence, it uses six different methods that are all executed. According to analysis conducted by the cybersecurity expert Marco Ramilli, Torri’s “sophistication is a level above anything we have seen before”.
11. A powerful IoT botnet is capable of surviving reboots
One of the common ways of removing malware from smart devices, routers, or modems is to simply reboot the device and have the memory wiped clean. That would bring the device back to its original state and prepare it for use again. But a new type of malicious IoT botnet, called Hide and Seek, can survive reboots and simply infects the device over and over again – a previously unseen feature that threatens to wreak havoc. The Hide and Seek botnet has already infected around 90,000 unique devices since January 2018 and could eventually be used for information theft, espionage, and extortion. And worse still, hackers are continuously enhancing its features. Bogdan Botezatu, a cybersecurity analyst, warns that “the botnet is undergoing constant redesign and rapid expansion” as it seeks to use infected devices to scan for other potential targets.

12. Stealing processing power to produce cryptocurrencies
Creating cryptocurrencies through a process known as ‘mining’ requires massive computing power and leads to high energy bills. So instead of doing all the heavy-lifting themselves, hackers have found a way to steal processing power by planting malware in people’s computers and smart devices. The only warning signal of infection, though, is reduced performance. These attacks, known as ‘cryptojacking’, are rapidly growing in frequency, as 59 per cent of organisations “have detected cryptomining malware on their systems at some point” and most detections occurred in the last six months.

Hackers are also becoming increasingly creative when it comes to planting malware. For instance, some disguise crypto-mining software as fake Adobe updates. They even target universities such as St. Francis Xavier University in Canada. Following the attack, this university had to shut down its network for a week to clean up the system. As long as the value of cryptocurrencies keeps growing, cryptojacking will remain a threat.
13. Russian WebCobra malware hijacks computers to mine crypto-coins
McAfee Labs, an internet security provider and a research lab, recently discovered new cryptojacking malware named WebCobra that apparently originates from Russia. Once planted into a victim’s computer, the malware steals processing power so that the hacker can run its crypto-mining software to produce Monero and Zcash cryptocurrencies. It’s unique in its ability to learn about the victim’s computer and deploy different codes for different operating systems. The only sign of malware is reduced performance of the infected computer and increased power consumption. The rise in ‘cryptojacking’ of this sort occurred at a time of rising cryptocurrency value, enabling hackers to sell the digital coins they mined for significant sums of money. In fact, mining malware cases have increased by almost 500 per cent in 2018 across the globe, and WebCobra has infected users in the US, South Africa, and Brazil and will remain a significant security threat.
14. The fileless crypto-miner PowerGhost is raiding corporate networks
A new type of crypto-mining malware, dubbed PowerGhost, was discovered by researchers from the cybersecurity and antivirus provider Kaspersky Lab. Much like WebCobra, it also infects computers and uses their processing power to produce cryptocurrencies for hackers. But unlike similar malicious programs, PowerGhost is actually fileless and doesn’t store mining software directly onto a disk, making it hard to detect. It can also automatically self-update and is designed to spread across the local network by copying itself. For now, the primary targets of PowerGhost have been corporations in Brazil, Columbia, India, and Turkey and not individual users. Kaspersky Lab warns that “As this trend grows, enterprises will be put at risk, as miners sabotage and slow down their computer networks, damaging overall business processes and lining their own pockets in the process.” Companies are advised to ramp up their cybersecurity, keep all software updated, and educate employees on the best IT protection measures.

15. Public services are under threat from ransomware attacks
Ransomware attacks have been plaguing the internet for the past few years, and this trend is set to continue in the future. Hackers use ransomware programs to encrypt user files and demand payment in exchange for the keys that unlock the data. But instead of spreading malware to as many computers as possible, attackers will focus more on a smaller group of more profitable targets such as hospitals, public utilities, and other institutions that deliver key public services. By causing a power outage or shutting off the water supply, they hope to force these organisations to pay large sums of money. For instance, the Hollywood Presbyterian Medicare Center paid hackers $17,000 in 2016 to regain control of their system. And as hackers exploit these vulnerabilities, their average payment demand is expected to increase by 6,500 per cent this year, “from an average of $300 to $20,000 per payment”.
16. Hackers might put smart cities under ‘cyber-siege’
A ransomware attack on the City of Atlanta’s digital operations in March 2018 showed just how vulnerable smart city infrastructure can be. Websites were shut down, bill-paying services turned off, and police dashcam video recordings wiped out. The sustained damage amounted to $17 million, but the authorities refused to pay the $51,000 ransom demand. Instead, they decided to take the hit, pay cyber experts to regain control over the system, and improve cybersecurity to prevent similar breaches in the future. A similar attack also struck the Port of San Diego in October 2018, forcing its staff to deactivate a part of the port’s system. The FBI and the Department of Homeland Security are still investigating the incident. These attacks demonstrate that while cities are becoming smarter in an attempt to provide better services to their growing populations, they fall short in efficiently protecting their digital infrastructure. To minimise the risk of further attacks, cities urgently need to invest in cybersecurity defenses.
17. Ransomware-as-a-Service makes cyber blackmail a lot easier
The costs related to ransomware damage are projected to grow to $11.5 billion this year, and Ransomware-as-a-Service (RaaS) plays a significant role in this trend. RaaS enables hackers to sell malware to other, less tech-savvy criminals, helping them to encrypt victims’ data and demand payments. Criminals can pay a fee to use the malware or split the victims’ payment with the hackers. For instance, Philadelphia, a ransomware hacking kit, was used to target highly specific organisations such as hospitals. Rainmaker Labs, the group behind Philadelphia, even uploaded a product walkthrough video on YouTube. Meanwhile, new types of RaaS tools are regularly hitting the market, including Saturn, a ransomware kit that requires no upfront payment as developers take a 30 per cent cut of the ransom payments. And as more and more criminals start to use RaaS software, we can expect an increase in ransomware attacks, making cyber protection a critical task for companies and individual users alike.
18. Ransomware hackers exploit human psychology
As if encrypting people’s data and demanding a payment wasn’t diabolical enough, some ransomware hackers have added a new twist. Popcorn Time ransomware, for instance, named after but unrelated to a bittorrent movie site, offers its victims three choices: pay the ransom, lose data, or “infect two other people in exchange for your decryption key”. This creates a moral dilemma and touches upon basic human instincts such as selfishness and ‘eat-or-be-eaten’. On a macro level, it also forces people to rethink whether infecting others or even paying the ransom, and thus encouraging hackers to ramp up attacks, is worth the damage it inflicts upon society.

Besides this, businesses blackmailed by ransomware have to take into account the fate of employees and their families in case if they refuse to pay and critical data is lost. Regardless of whether Popcorn Time succeeds in exploiting human psychology, it’s an example of increasingly creative and sophisticated tactics hackers deploy in an attempt to threaten people and extort money.
19. Highly effective fileless malware attacks are on the rise
Almost 80 per cent of successful attacks in 2017 were carried out using fileless malware, a type of malicious software that doesn’t store files onto a disk but runs them in the memory. For instance, it hijacks the Windows shell and script language PowerShell to execute commands and infect other machines. And since fileless malware isn’t installed in a typical way and uses trusted programs to run, it’s hard to detect. “Two thirds of security researchers said they were not confident legacy antivirus software could protect their organizations”. That’s why cybersecurity companies are turning to machine learning and other cutting-edge technologies to combat this threat. Hackers use the fileless technique for various purposes, such as deploying “financial Trojans and cryptocurrency miners”, and these attacks are reportedly increasing by seven per cent per month. And as their effectiveness is well-documented, it’s likely that more and more of these sophisticated fileless attacks will be launched worldwide in the future.
20. Facial recognition systems and touch ID sensors aren’t as secure as we think
Biometric data such as fingerprints and facial images are considered a more secure method of authentication than traditional passwords. But they, too, can be stolen and misused, warns Experian, a consumer credit reporting agency. In fact, researchers at New York University have developed AI software that’s capable of fooling fingerprint protection systems around 20 per cent of the time. And security experts at Bkav, a Vietnam-based tech corporation, claim they’ve tricked iPhone X’s Facial ID by creating a composite mask of a victim’s face. Biometric data can also be stolen on a mass scale. For instance, hackers stole 5.6 million fingerprints from the US Office of Personnel Management, proving that determined hackers with sufficient resources and enough time can hack just about anything. Emboldened by these successes, cyber-criminals are poised to increasingly focus on biometric hacking and expose the vulnerabilities of existing security systems.

21. Protecting systems with biometric data alone is a major risk factor
Using biometric data such as fingerprints, faces, voices, or irises as the only authentication factor puts users at great risk. After all, this data is often in the public domain. People leave fingerprints everywhere, and our pictures are all over social media, in governmental databases, and many other places. Hackers can use all of these to recreate our biometric features for criminal activities. Nevertheless, solving this issue is surprisingly simple and involves adding one or two more layers of authentication such as complex passwords and limiting login based on the IP address or device type. Despite the obvious advantages of two- or multi-factor authentication, a significant number of people will most likely keep using single-factor biometric authentication and hackers are expected to “take advantage of their naiveté and pull off major biometric hacks”.
22. State-sponsored cyber-attacks are bound to increase
Pulling off a major cyber-attack often requires resources that individual hackers can rarely afford. Many large-scale attacks are therefore sponsored by states well-known for this type of behaviour, such as China, Russia, Iran, Israel, North Korea, and the US. Governments and intelligence agencies rely on hacking to acquire high-value political, industrial, and military data as well as to disrupt electronic voting systems and manipulate public opinion. Authorities are increasingly vigilant in the fight against these threats. The US, for instance, has banned the use of Kaspersky software in government agencies, accusing this antivirus provider of being under Kremlin’s influence. The UN is planning to implement a Cyber Security Treaty to address the problem of state-sponsored cyber-attacks. Not everyone is convinced this will work, however, and the cybersecurity expert Ian Kilpatrick argues that “nation-state sponsored espionage, cyber-crime and sabotage will continue to expand”.

23. AI-driven malware mimics the behaviour of human hackers
When we think of cyber-attacks, the first image that springs to mind is a hacker sitting in front of a computer, trying to gain access to someone’s files. While many hacks are still performed by individuals, they’re becoming increasingly refined, and yes, automated. Researchers from the AI company Darktrace claim that AI-based cyber-attacks have evolved, making it difficult for security experts to distinguish AI-powered attacks from those performed by humans. As the researchers reveal, malicious AI software can imitate the behaviour of human hackers to avoid detection. A team from Darktrace envisioned several scenarios in which a computer is infected with AI malware – a virus that observes the computer’s behaviour and environment and adapts accordingly. In one of the scenarios, the AI malware was used to steal data from a company specialising in medical technology. This was done slowly and in phases, so it was almost impossible to detect that anything strange had happened. Researchers warn that “defensive cyber AI is the only chance to prepare” for these scenarios.
24. AI – the most efficient hacking tool
The benefits of artificial intelligence are well-known. Besides automating various industries, AI can also help organisations detect cybersecurity risks. In fact, 87 per cent of cybersecurity professionals in the US rely on AI. Of course, this tech can also easily fall into the wrong hands. Research shows that 91 per cent of cybersecurity professionals are concerned about hackers using AI to conduct more complex cybercrime.

To reveal threats associated with AI cyber-attacks, IBM Research developed ‘DeepLocker’ – malware that conceals its intent until it reaches a specific victim. Most malicious viruses usually attack an unspecified number of computers, but DeepLocker is a bit different. It harnesses the power of AI to stealthily reach the right target, after which it infects the victim’s computer system. Thanks to facial recognition tech, geolocation, or speech recognition, DeepLocker can identify the owner of the device, and only then decide whether to attack the system.
25. Self-driving vehicles are also prone to hacking
Our computers, smartphones and other smart devices aren’t the only ones that can be hacked. The same can happen – and has already happened – to (autonomous) vehicles. Back in 2015, two researchers managed to hack a Jeep Cherokee and take control of its steering wheel. This particular experiment was conducted on a non-self-driving car, but that doesn’t mean autonomous vehicles are immune to similar attacks. According to Bryson Bort, the founder of the cybersecurity consultancy Grimm, there are two ways to hack a self-driving car. The first is through physical contact with the car, and the second is remotely, via the internet. As Bort explains – and as you can imagine – hacking a car can cause untold damage and chaos. A hacker accessing a vehicle’s system can manipulate the car’s behaviour, leading to accidents and loss of life.
Cybersecurity in the future
While we’re reaping the benefits of smart tech and digitalisation, we should also be aware of the risk of cyber-attacks. Privacy concerns and frequent data security breaches are pressuring developers to think ahead and work out solutions to prevent cyber-attacks. This, however, is a real challenge. As technologies keep maturing and morphing into super-intelligent, almost self-sustainable systems, it will become more difficult to predict how, where, and when malicious cyber-threats could occur.
What if someone hacks our AI-powered car? What if a smart computer virus starts learning and acting completely independently? In theory, we’d be able to teach smart programs to detect other clever programs with malicious intent and react accordingly, but this will be an ongoing ‘battle royale’ between intelligent programs. For now, prevention, detection, and counteraction are still the best measures against cyber-attacks.
Share via:


