- The rise of cybercrime
- The lack of a legal framework
- Cyberspace as a warfighting domain
- Stuxnet, the world’s first cyber weapon
- How powerful are cyber weapons?
- The most devastating cyber-attack in history
The world has become increasingly connected over the years, which had a profound impact on many different aspects of our lives. Our culture, finance, energy, transportation, education, healthcare, and communications are becoming more and more dependent on the internet, and while it provides us with unparalleled levels of convenience, it’s also making these systems more vulnerable to attacks from the outside. At the same time, hackers are becoming increasingly inventive and bold, their attacks more sophisticated and destructive, to the point that they’re now posing a major threat to the economic, political, and social stability of our world. It’s not too difficult to imagine that the war of the future will not be fought in the trenches, but rather in the depths of the World Wide Web, and it will be far more frightening than you can imagine. Welcome to the age of cyberwar.
The rise of cybercrime
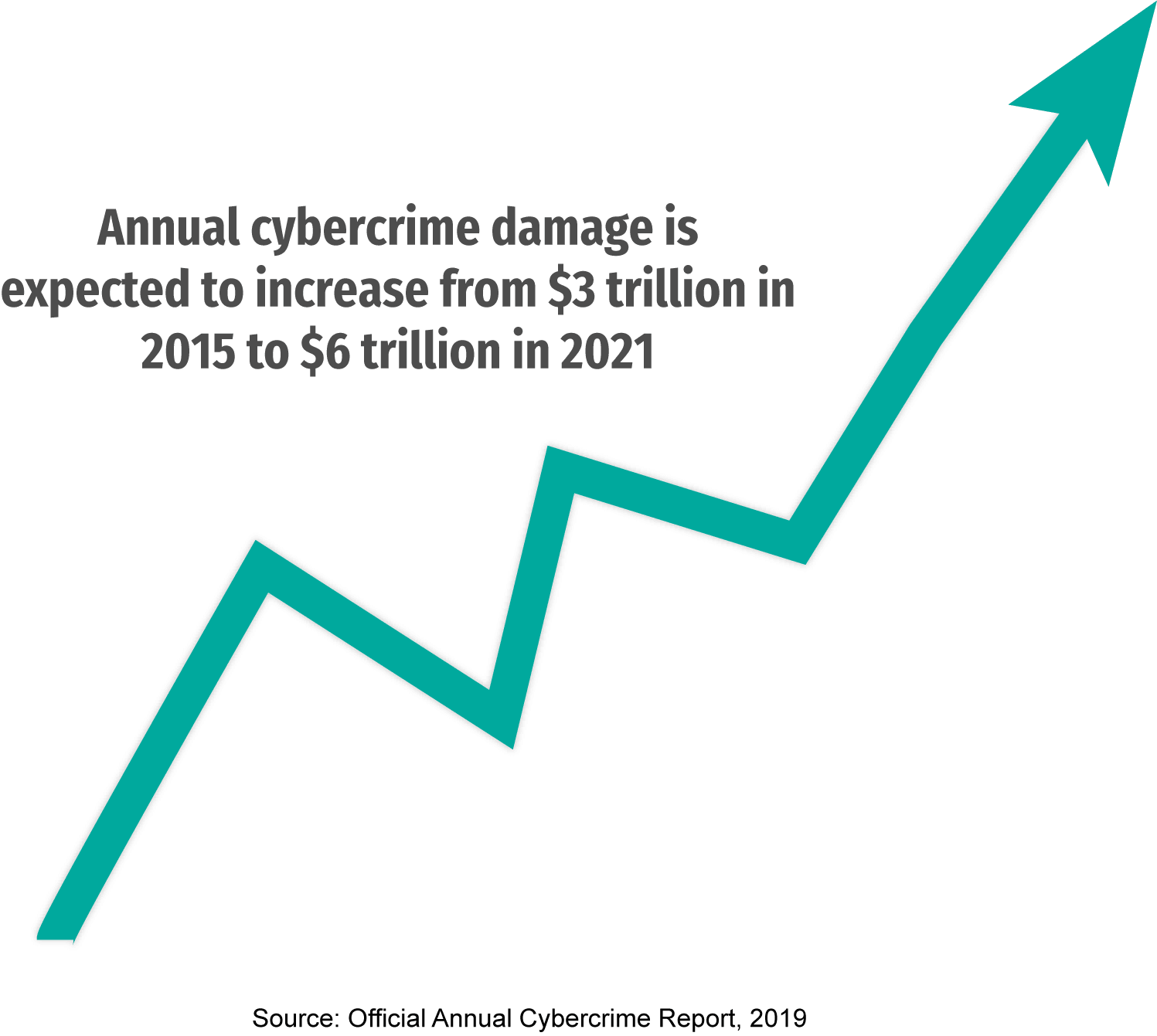
Cybercrime has become one of the world’s most pressing issues in recent years. According to the 2019 Official Annual Cybercrime Report, published by Cybersecurity Ventures, annual cybercrime damage is expected to increase from $3 trillion in 2015 to $6 trillion in 2021. “DDoS attacks, ransomware, and an increase in zero day exploits are contributing to the cybercrime damages prediction becoming a reality,” says Robert Herjavec, the founder and CEO of the global cybersecurity firm Herjavec Group. However, not every cyber-attack can be considered an act of cyberwar. A lone hacker or a group of hackers stealing money from your personal bank account wouldn’t qualify as cyberwar, but those same hackers employed by a country to take down another country’s banking system to destabilise its economy would.

In the broadest terms, an act of cyberwar can be defined as one country’s attack on another country’s digital infrastructure. Some would also add that, to qualify as an act of cyberwar, a cyber-attack has to cause damage comparable to that of a physical attack. According to NATO, there are two main types of cyber-attack that can be characterised as cyberwar: cyber-enabled espionage and cyber-enabled sabotage. However, the debate is still ongoing whether the former should be considered an act of cyberwar at all. And that’s precisely the main problem when talking about this subject. There are so many grey areas that nobody really knows when the line that differentiates a regular cyber-attack from an act of cyberwar is crossed. When is it justified for a country to respond to a digital attack with physical force? And this uncertainty is making many people nervous, because not knowing where the line is means that any incident could quickly spiral out of control and turn into a real-world conflict.
The lack of a legal framework
There are currently no international laws or treaties that refer to cyberwar or stipulate how countries can respond to a cyber-attack. However, under international law, countries are allowed to respond to armed attacks with force. That means that, in theory, a country could justifiably use its military arsenal to react to a cyber-attack that caused major destruction or led to loss of life. Thankfully, no attacks have reached that threshold yet. Still, even with this in mind, there’s a great deal of uncertainty surrounding the whole matter. Some countries are even taking advantage of the lack of a legal framework to experiment with their cyberwar techniques in the real world, knowing they’ll probably be able to get away with it.

Looking to bring some clarity and eliminate the grey areas surrounding cyberwar, a group of scholars put together a book called the Tallinn Manual, which aims to explain how international law can be applied to cyber warfare. Backed by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCoE), the Tallinn Manual is aimed at everyone from legal advisers to governments, military, and intelligence agencies and consists of 154 rules that attempt to clarify when a cyber-attack constitutes a breach of international law, helping them determine the proper response to such attacks.
Cyberspace as a warfighting domain
As the world’s governments become increasingly aware of the dangers posed by cyber-attacks, they’re stepping up their efforts to improve their cyber capabilities, not only to defend themselves from such attacks, but also to use them against their enemies if necessary. In fact, many countries now consider cyber capabilities as an essential part of their operational military capability and their strategic toolbox. In a joint statement, US intelligence chiefs recently revealed that more than 30 countries of the world, including Russia, China, Iran, and North Korea, are currently building offensive cyber-attack capabilities.
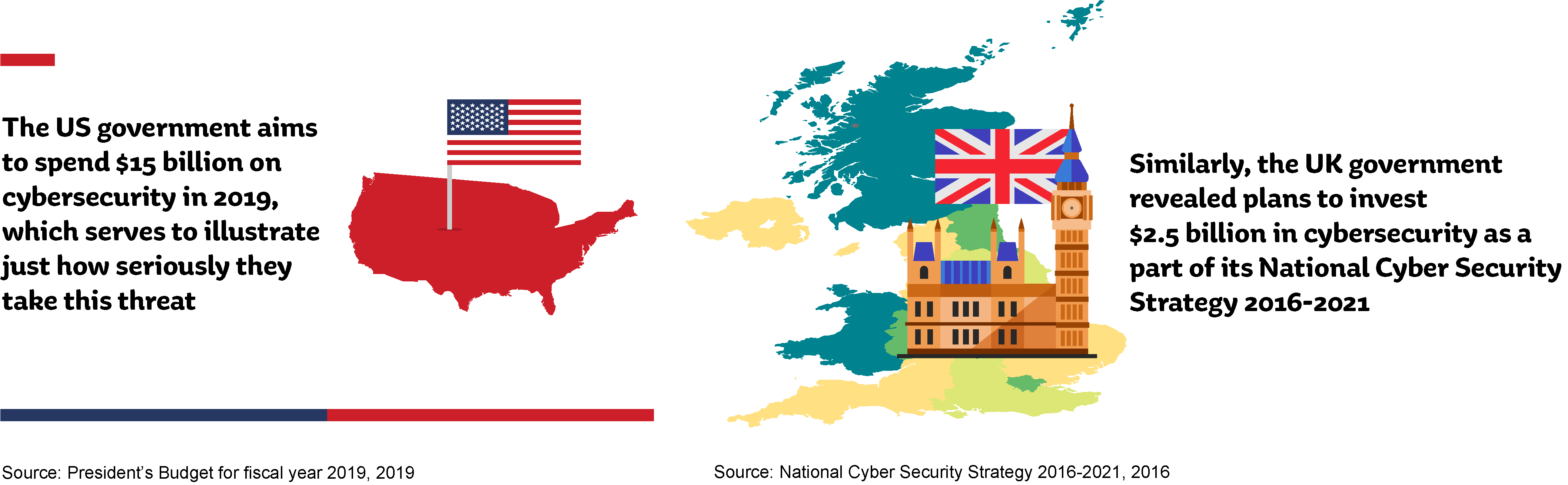
The US government aims to spend $15 billion on cybersecurity in 2019, which serves to illustrate just how seriously they take this threat. Similarly, the UK government revealed plans to invest $2.5 billion in cybersecurity as a part of its National Cyber Security Strategy 2016-2021.
At the Warsaw Summit in 2016, cyberspace was officially recognised as a warfighting domain by the members of NATO, alongside ground, air, sea, and space. Furthermore, NATO has committed itself to using its full cyber capabilities to defend its members against any computer-based attacks.
Stuxnet, the world’s first cyber weapon
So, what does a cyber weapon look like, exactly? Reportedly developed in cooperation between the United States and Israel, although both governments have officially denied any involvement, Stuxnet was the world’s first digital weapon. It was a malicious computer worm designed to sabotage Iran’s nuclear program. Stuxnet targeted specific Siemens industrial control systems and ended up inflicting physical damage to more than a thousand centrifuges in the Iranian uranium enrichment program. However, it remains unclear whether the attack had any major impact on the program other than causing delays. Stuxnet was an incredibly sophisticated piece of software that took years of research and millions of dollars of investment to develop. It used four different zero-day exploits, bugs in the code that still haven’t been discovered and patched by the developer, to gain access to and take control of the targeted systems.

To breach Iran’s network, the attackers first infected several computers that were outside of the network but believed to be connected to it, hoping they’d spread the infection further. While ultimately successful, this approach had one unintended consequence – the infection spread far beyond the original target and affected computers all over the world. And that’s one of the main problems associated with cyber weapons. Their creators can easily lose control of them and cause far more damage than initially intended. Furthermore, cyber weapons leave traces and can later be analysed, reverse engineered, and used against the country that developed them. The US learned this the hard way when the hacking collective called the Shadow Brokers somehow obtained and then leaked highly classified information about cyber weapons stockpiled by the National Security Agency (NSA). These were later used by various hacker groups to attack a wide variety of targets within the United States and all over the world.
How powerful are cyber weapons?
In December 2015, a group of Russian hackers called Sandworm launched a series of attacks on Ukraine’s energy grid, leaving hundreds of thousands of people without electricity for hours at a time. It was the same group of hackers who had relentlessly been attacking the country for months, disrupting almost every sector, including the government, military, transportation, finance, media, and energy. According to Petro Poroshenko, the President of Ukraine, more than 6,500 cyber attacks on 36 different targets had been registered in less than two months.
The attack on the energy grid was a culmination of these efforts. The hackers used a trojan called BlackEnergy to gain access to the power companies’ networks and the software that allows users to control equipment like circuit breakers remotely and cut the power. Then they disabled legitimate operators from regaining digital control of the breakers by rewriting the firmware in the sub-stations’ converters, used the well-known data destruction program called KillDisk to destroy their computers’ hard drives, and disrupted the stations’ battery backups.
The attacks resumed in the fall of 2016, hitting the country’s pension fund, treasury, railway company, seaport authority, and the ministries of infrastructure, defense, and finance, once again culminating with an attack on the energy grid. This time, the blackout lasted for about an hour, which is how long it took the operators to bring the power back online manually. The second attack on the energy grid was far more sophisticated than the first one. It was executed using an adaptable piece of malware called CrashOverride, which was designed specifically to target energy grids and is capable of independently sabotaging physical infrastructure.
What’s particularly frightening about these attacks is that the hackers retreated before they caused the maximum possible damage. When security experts later analysed the code, they discovered that the hackers had the means to damage the grid permanently, but chose not to. Why? For some, it’s a clear indication that the Russians were simply using Ukraine as a testing ground, saving their worst for Russia’s real adversary – the United States. “They’re testing out red lines, what they can get away with,” says Thomas Rid, a professor in the War Studies department at King’s College London. “You push and see if you’re pushed back. If not, you try the next step.”
The most devastating cyber-attack in history
Sandworm struck again in June 2017. The attack originated at a small Ukrainian software company called Linkos Group, whose servers were hijacked by hackers and used to infect thousands of computers all over the country with a piece of malware called NotPetya. NotPetya used two powerful hacker exploits to gain access to the computer system, EternalBlue and Mimikatz. EternalBlue is a penetration tool originally developed by the NSA and later leaked by the Shadow Brokers, which allows attackers to run their own code on any unpatched machine. Mimikatz, on the other hand, enabled them to retrieve passwords from the computer’s memory and use them to gain access to other machines that use the same credentials. Once the system was breached, NotPetya would permanently destroy all data on it by encrypting the computers’ master boot records.
According to Information Systems Security Partners, a Ukrainian cybersecurity company, the hackers hit more than 300 companies and wiped approximately 10 per cent of all computers in the country. The attack paralysed transportation, power companies, hospitals, airports, federal agencies, banks, ATMs, and card payment systems across the country. This time, however, the damage wasn’t contained to Ukraine. Within hours, it spread far beyond its original target and infected thousands of computers around the world, including those that belonged to some of the world’s largest companies, such as the largest global shipping conglomerate Maersk, the pharmaceutical giant Merck, the French construction company Saint-Gobain, FedEx’s European subsidiary TNT Express, the manufacturer Reckitt Benckiser, and the food producer Mondelēz. The White House estimates that the total damage of the NotPetya attack amounted to $10 billion, making it the most devastating cyber-attack in history. “While there was no loss of life, it was the equivalent of using a nuclear bomb to achieve a small tactical victory,” says Tom Bossert, a former Homeland Security adviser.
Increased connectivity may have made our lives easier and more convenient, but it’s also made us more vulnerable to cyber-attacks. There practically isn’t a single aspect of modern society that doesn’t rely on the internet to a certain extent. Some countries have recognised this as an opportunity to inflict damage to their political opponents without formally declaring war, as evidenced by the increase in the number of attacks against the world’s digital infrastructure over the years. Does that mean that we’re on the verge of an actual, full-scale cyberwar? That’s difficult to say at this point. There’s still a great deal of uncertainty about the whole matter, which is even further complicated by a lack of a legal framework. No one is really sure where the line that separates a regular cyber-attack from an act of cyberwar is drawn. Some countries are taking advantage of this to see how far they can push before someone retaliates. And that’s where the danger lies. Until we have laws that will clarify what cyberwar really is and eliminate grey areas, just about any incident could theoretically spiral out of control and result in a real-world conflict.
Share via:


