- What is this NotPetya attack and how does it work?
- Which countries and organisations have been affected so far?
- Who is behind these attacks and what is their objective?
- Why we should be afraid – very afraid – of these and similar cyber attacks
- We need to invest in a cyber militia
- What can be done to combat ransomware and similar attacks?
A sophisticated global cyber attack is currently causing major upheaval for businesses and organisations around the world. According to security experts, the ‘not-really-ransomware’ NotPetya is believed to have infected computers via MeDoc accounting software in Ukraine, using the EternalBlue hacking tool. This tool is widely believed to have been stolen from the NSA and was also used in last month’s WannaCry ransomware attack, which infected hundreds of thousands of computers across more than 150 countries. With the ability to take out a staggering 5.000 computers in less than ten minutes, this week’s attack is much more sophisticated than last month’s WannaCry.
Free trendservice
What is this NotPetya attack and how does it work?
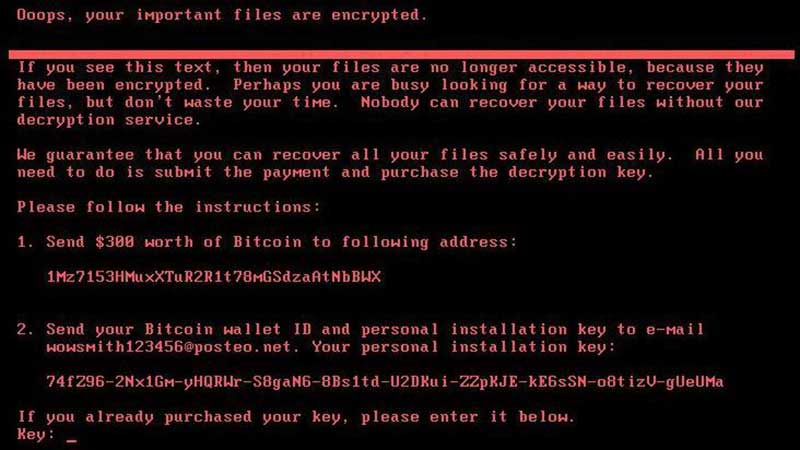
The attack, which began on Tuesday, was first noticed in the Ukrainian energy, telecom and media sector where computer screens suddenly went black, simply displaying a message demanding $300 in return for a key to decrypt the locked files. According to security experts at Kaspersky, Microsoft and ESET as well as the Ukrainian Cyber Police, the infection was seeded by hijacking the updating process in Ukrainian accounting software MeDoc, which is used by various organisations across the world. As soon as one computer in a network is infected, the virus automatically and rapidly spreads to the rest of the network. In a statement on Facebook, MeDoc however denied any involvement.
The virus was able to spread due to the fact that businesses have failed to adequately secure their networks and install regular Windows updates. This enables increasingly aggressive cyber criminals to shut down government and corporate networks and cripple critical infrastructure. Although the virus appears to share a significant amount of code with the older Petya ransomware, experts agree that the resemblance is only superficial and that it is not in fact ransomware. Meanwhile, the malware has been dubbed NotPetya by Russia’s Kaspersky Lab. Other, tongue-in-cheek versions of the name floating around the Internet now include Petna, Pnyetya and Goldeneye.
Which countries and organisations have been affected so far?
Businesses, organisations and infrastructure that have come under attack include banks, government offices, petrol stations, shipping companies, pharmaceutical firms, food manufacturing companies, metro systems and oil and gas companies across, among others, the Ukraine, Russia, the US, India and Australia as well as European countries including the UK, Spain, Norway, Germany, Portugal, France, Denmark and the Netherlands.
In Ukraine, where the ‘ransomware’ allegedly originated, the central bank, government departments, a state-run aircraft manufacturer, the metro network and the airport in Kiev have all been paralysed by the hacks. In Norway, the cyberattack is affecting an unnamed international company, according to the country’s national security authority. Danish logistics and transport company Maersk, with branches worldwide, announced that multiple business units and websites had been shut down.
Other organisations affected by the cyber attack include food company Mondelez, Royal Canin – the pet food unit of the candy manufacturer Mars Inc., the monitoring system of the Chernobyl power plant, US pharmaceutical giant Merck, British advertising firm WPP, global law firm DLA Piper, Netherlands-based transport company TNT Express, French construction materials firm Saint-Gobain and Russian oil and steel firms Rosneft and Evraz and Heritage Valley Health System – which runs healthcare facilities and hospitals in Pittsburgh.
Maersk and APM – 17 shipping container terminals hacked globally
Danish shipping company A.P. Moller-Maersk, which handles one out of seven containers shipped around the globe, said the cyber attack affected all of their business units, including oil and gas production, drilling services, port and tug boat operations, oil tankers and container shipping. APM Terminals, Maersk’s port operator, was also affected. Due to computers being infected by ransomware, 17 shipping container terminals had been hacked; 2 in Rotterdam and 15 in other parts of the world. Maersk said that it was unable to process new orders after having been hit by the cyber attack. According to a Dutch Maersk employee, who wishes to remain anonymous, the situation is even more dire. He said: “Within one hour, all systems were down. Approximately 50 terminals have been hit, in Europe, Asia and North and South America.”
Dutch port economist Peter de Langen says: “There are thousands of containers on board of these ships. They’re filled with clothing, electronics, parts and raw materials for factories. If these ships fall one day behind schedule, five percent of people and companies who have ordered goods are already in trouble. As the delay increases, it takes longer for the ships to catch up with the timetable. The secondary effects are huge.”
De Langen’s colleague, Bart Kuipers, adds: “Container terminals have been highly automated in recent years. They’re practically IT companies. If the computers crash, the terminals shut down. The computers determine which containers need to be loaded or offloaded and where they go. The APM terminal on the Second Maasvlakte is one of the most modern in the world. It’s state of the art, also in terms of security policy. The fact that these terminals are affected says a lot about the vulnerability of all companies. This is dramatic.”
Cyber attack update 09:06 CEST pic.twitter.com/kInQZz4Wyv
— Maersk (@Maersk) June 28, 2017
Cadbury chocolate factory system in Australia goes down
The Cadbury chocolate factory in Tasmania was also hit and production was halted when the company’s IT system went down in the cyber attack. John Short, Australian Manufacturing Workers’ Union state secretary, said he was under the impression that Cadbury’s computer system had sophisticated virus protection in place, as it is a highly advanced and automated company. Cadbury’s parent company, Mondelez International, has stated that they are not sure how long it will take to fix the problems and when their systems will be restored. “We continue to work quickly to address the current global IT outage across Mondelez International,” the company said. “Our teams are working offline in an effort to maintain business continuity with our customers and consumers around the world. We will share updates with our suppliers and partners as they become available. At this time, we do not know when our systems will be restored but we appreciate everyone’s patience, understanding and partnership during this process.”
The #Cadbury factory in Tasmania is the first large scale Australian business to be shut down by #Petya #ransomware https://t.co/ayGxmIme6C
— AWD Melbourne (@itmelbourne) June 29, 2017
Tens of thousands of computers affected at major US drug manufacturer
A spokesperson of a major US pharmaceutical company reported that the NotPetya attack is extremely serious and sophisticated. As they have installed state-of-the-art security systems and have always been well-prepared, they had never been affected by this type of attack before. They’ve had to fly in experts to assess the damage. The entire IT system and critical servers will need to be isolated, checked and have programs re-installed. In these cases, even individual and personal computers and laptops have to be switched off in order to prevent further spread of the infection.
Property arm of France’s biggest bank BNP Paribas affected by extortion campaign
According to Reuters, the cyber attack also hit the property subsidiary of BNP Paribas, which provides advisory, investment and property management services. Some employee computers had been blocked as a result of the incident but measures had been put in place to stop the attack in its tracks. Even though many organisations affected internationally had connections to Ukraine, this does not seem to be the case for the French bank. It does however own UkrSibbank in Ukraine. Compared to other industries, banks generally have more sophisticated cybersecurity systems in place than other industries and in 2015, BNP Paribas even launched a ‘transformation program’ for the upgrade of their security systems.
TMF Group affected by ransomware virus
The TMF Group, a leading global provider of high-value business services with 100.000 customers worldwide, also confirmed that it has been affected by the ransomware virus at its facilities across the globe. The group is operational in over 80 countries. A TMF Group official said: “We confirm that TMF Group is experiencing IT issues related to the virus currently affecting many businesses around the world. We have taken our systems down as a precaution as we continue to investigate the full extent of these issues. We will issue updates on a regular basis as we have more clarity around impact.”
German skincare company Beiersdorf’s IT and phone systems under attack
The German manufacturer of Nivea skin care products, Beiersdorf, also said it had been under attack from the ransomware, affecting the company’s telephone and IT systems globally. According to a spokeswoman, the firm had immediately implemented measures to keep the impact to business partners and customers to a minimum.
Reckitt Benckiser fallen victim to the cyber attack
Hygiene products manufacturer Reckitt Benckiser, producer of well-known brands Lysol and Dettol, has confirmed that it, too, has fallen victim to the global ransomware attack. The company is working round the clock to contain the virus and recover their systems. They hope to restore their business operations as soon as possible.
A massive #cyberattack has affected global firms including #WPP, #Mondelez and #ReckittBenckiser https://t.co/XcsE5JxyLg pic.twitter.com/oCf6FR1QUd
— European Supermarket Magazine (@esm_magazine) June 28, 2017
Who is behind these attacks and what is the objective?
It’s still too early to say who’s responsible for unleashing NotPetya and why. Because the virus is incredibly sophisticated, security experts speculate that we might be dealing with a government, although this is very hard to prove. Information Security researcher The Grugq points out that the email address listed as a payment contact for the perpetrators was hosted with a German company. Within several hours, however, when its criminal use came to light, access to the email address was blocked. So far, only a few thousand dollars in ransom payments have been received in the associated Bitcoin wallet.
The motive for this attack, allegedly ‘disguised’ as ransomware, certainly does appear to be focused on causing as much possible damage in the shortest possible time. The Grugq said, “This is definitely not designed to make money. This is designed to spread fast and cause damage, with a plausibly deniable cover of ransomware.”
Why we should be afraid – very afraid – of these and similar cyber attacks
Last month’s WannaCry and this week’s NotPetya attack have probably already caused billions worth of damage. But this is only the beginning. Hacks of this nature are becoming increasingly sophisticated and will, in the future, undoubtedly include even more critical infrastructure like water treatment plants, power companies, public transportation systems and healthcare facilities. In 2016, a staggering 14 medical facilities in the US fell victim to cyber attacks in which systems had been infected with ransomware. Many of these institutions actually paid the ransom to have their systems restored. In February 2016, the data at the Hollywood Presbyterian Medical Centre was held hostage by ransomware until the centre paid the Bitcoin equivalent of $17,000. The hackers had knocked the centre offline for almost an entire week, affecting everything from emails to CT scans, and staff had to resort to handwritten notes and faxes.
It has already been proven that self-driving cars can be hacked, and even medical devices such as insulin pumps aren’t safe. Advances in implantable medical devices will make them increasingly popular and widespread, and they will all be connected to the Internet of Things to provide physicians with important patient information. Cyber criminals can exploit these devices to target individuals and hospitals, causing heart attacks, seizures, insulin comas and any other type of unimaginable damage.
We need to invest in a cyber militia
These attacks are setting off alarm bells around the world about the need to improve our digital defenses. One of the biggest stumbling blocks seems to be the impossibility to create awareness among city councils, mayors and stakeholders. And getting the right people to make budgets available to secure cities and infrastructures is an even tougher challenge. A lot of time needs to be invested in convincing these parties of the severe lack of security of our systems. We know how to evacuate a soccer stadium when there’s a huge fire, but if the city is shut down because of a computer hack, the disaster is unimaginable. We need digital evacuation plans in case we’re faced with a large scale-cyber attack. We don’t have anything like that in place as of yet.
According to Dr David Day, cyber security expert and senior lecturer at Sheffield Hallam University, this week’s attack is just the tip of the iceberg. He said: “Basically the NSA have created something which can be used as a weapon. That weapon has been stolen and that weapon is now being used. This underlines the whole need for debate over privacy versus security. The NSA will argue that the tool was developed with a need to ensure privacy, but actually what it’s being used for is a weapon against security.”
These attacks are a sign again of how connected we are as a community. In the future, we are going to be even more connected, not less. That means we need to step up our efforts to protect ourselves. We need a new vision. We need a complete overhaul of our current systems, organisations, and processes. Governments around the world need to invest in a cyber militia or vigilante and cohesive policies for how we can legally respond to attacks of this nature. We need to proactively address the cyber threats facing us and formulate government responses to help start creating proper deterrences.
What can be done to combat ransomware and similar attacks?
Since the NotPetya virus doesn’t seem to be spreading randomly, as was the case with WannaCry, it appears that mainly businesses, organisations and critical infrastructure are the targets of this massive attack.
It should be obvious that vulnerabilities are not easy to remedy. We can’t simply disconnect our lives, too much depends on connectivity, and disconnecting pacemakers or unwiring our cars just isn’t feasible. And since restricting connectivity is neither reasonable nor economically desirable, we must learn to live with a certain amount of danger. We can’t eliminate the threat of cyber attacks completely, but we can take long overdue steps to close and lock many of the doors that cyber criminals now find open and waiting.
Counter-cybercrime agencies and government officials need to re-access connectivity to critical systems and consider physically isolating the most sensitive ones. They need to mandate immediate upgrades of computer and security systems. Furthermore, engagement with industry needs to take place, to assess the risk of hijacking of mass-transit and infrastructure of all kinds: power production and distribution, water treatment and medical services. A previous large-scale hack of a Ukrainian power plant exposes the risk of fully digital, connected monitoring systems. It is of critical importance that governments also acquire human monitors with analogue secondary systems that are not in any way connected to the Internet.
In terms of practical measures we can take ourselves, security experts advise users not to click on suspicious links and email attachments. Important steps to protect ourselves from ransomware attacks include installing new computer updates regularly, backing up important files and avoiding dubious downloads and websites.







